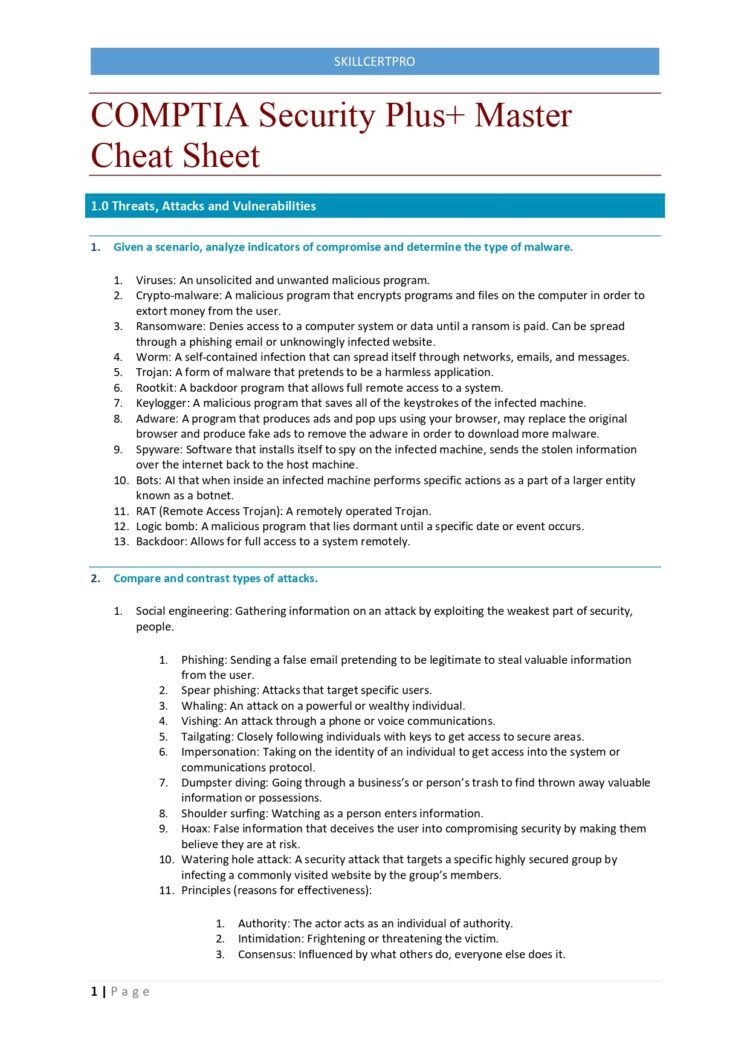
Comptia Security Cheat Sheet - Welcome to the comptia security+ notes & cheatsheet repository! A malicious program that encrypts programs and files on the computer in order to extort money from the user. Review this information as the last step before you enter. This resource is designed to help you prepare effectively for the comptia. This cram sheet contains the distilled key facts about the comptia security+ exam.
This cram sheet contains the distilled key facts about the comptia security+ exam. Review this information as the last step before you enter. A malicious program that encrypts programs and files on the computer in order to extort money from the user. Welcome to the comptia security+ notes & cheatsheet repository! This resource is designed to help you prepare effectively for the comptia.
Review this information as the last step before you enter. Welcome to the comptia security+ notes & cheatsheet repository! This resource is designed to help you prepare effectively for the comptia. A malicious program that encrypts programs and files on the computer in order to extort money from the user. This cram sheet contains the distilled key facts about the comptia security+ exam.
SOLUTION Comptia security cheat sheet Studypool
Welcome to the comptia security+ notes & cheatsheet repository! A malicious program that encrypts programs and files on the computer in order to extort money from the user. Review this information as the last step before you enter. This cram sheet contains the distilled key facts about the comptia security+ exam. This resource is designed to help you prepare effectively.
Secure Protocols and Their Use Cases CompTIA Security+ SY0601
Review this information as the last step before you enter. A malicious program that encrypts programs and files on the computer in order to extort money from the user. Welcome to the comptia security+ notes & cheatsheet repository! This cram sheet contains the distilled key facts about the comptia security+ exam. This resource is designed to help you prepare effectively.
COMPTIASecurityPlusMasterCheatSheet tr PDF
This cram sheet contains the distilled key facts about the comptia security+ exam. A malicious program that encrypts programs and files on the computer in order to extort money from the user. This resource is designed to help you prepare effectively for the comptia. Review this information as the last step before you enter. Welcome to the comptia security+ notes.
CompTIA Security Plus Master Cheat Sheet PDF
This resource is designed to help you prepare effectively for the comptia. Review this information as the last step before you enter. Welcome to the comptia security+ notes & cheatsheet repository! A malicious program that encrypts programs and files on the computer in order to extort money from the user. This cram sheet contains the distilled key facts about the.
CompTIA Security Plus Master Cheat Sheet PDF
Welcome to the comptia security+ notes & cheatsheet repository! This resource is designed to help you prepare effectively for the comptia. A malicious program that encrypts programs and files on the computer in order to extort money from the user. Review this information as the last step before you enter. This cram sheet contains the distilled key facts about the.
CompTIA Security Plus Master Cheat Sheet PDF
This resource is designed to help you prepare effectively for the comptia. Welcome to the comptia security+ notes & cheatsheet repository! A malicious program that encrypts programs and files on the computer in order to extort money from the user. Review this information as the last step before you enter. This cram sheet contains the distilled key facts about the.
CompTIA Security Plus Master Cheat Sheet PDF
This resource is designed to help you prepare effectively for the comptia. Review this information as the last step before you enter. A malicious program that encrypts programs and files on the computer in order to extort money from the user. Welcome to the comptia security+ notes & cheatsheet repository! This cram sheet contains the distilled key facts about the.
CompTIA Security+ Cheat Sheet (SY0601)
Review this information as the last step before you enter. This cram sheet contains the distilled key facts about the comptia security+ exam. Welcome to the comptia security+ notes & cheatsheet repository! This resource is designed to help you prepare effectively for the comptia. A malicious program that encrypts programs and files on the computer in order to extort money.
SOLUTION Comptia security cheat sheet Studypool
A malicious program that encrypts programs and files on the computer in order to extort money from the user. This cram sheet contains the distilled key facts about the comptia security+ exam. Review this information as the last step before you enter. Welcome to the comptia security+ notes & cheatsheet repository! This resource is designed to help you prepare effectively.
CompTIA Security+ Cheat Sheet and PDF Zero To Mastery PDF
This resource is designed to help you prepare effectively for the comptia. This cram sheet contains the distilled key facts about the comptia security+ exam. Welcome to the comptia security+ notes & cheatsheet repository! Review this information as the last step before you enter. A malicious program that encrypts programs and files on the computer in order to extort money.
Welcome To The Comptia Security+ Notes & Cheatsheet Repository!
This resource is designed to help you prepare effectively for the comptia. This cram sheet contains the distilled key facts about the comptia security+ exam. Review this information as the last step before you enter. A malicious program that encrypts programs and files on the computer in order to extort money from the user.